Every now and then, some teens or wannabe hackers (or real ones) run a de-auth attack on the wifi signals hoping to grab a password packet and then attempt to decrypt (usually by dictionary base / brute force attacks). There are 2 different negative effects to that: you get randomly disconnected from your wifi, and if you password is not strong, someone could eventually get on your network.
You will need a few things to be able to capture such unwanted traffic:
- A linux based machine, ideally Kali Linux as it has all the tools pre-installed
- A wifi adapter that supports monitoring mode. I use a USB WiFi dongle.
- Wireshark application
- Aircrack-ng tools
- Your wireless lan interface name (you can use
ifconfigorip a). Let’s say mine iswlan0 - The mac address of your wifi router. Let’s say mine is
AA:AA:AA:AA:AA - The channel of the BSSID of your wifi. Let’s say mine is 123
Monitoring mode
In order to capture packets, you need to set your wlan interface on monitoring mode. To do so:
airmon-ng start wlan0
Setup wireshark
Start wireshark and enter the following filter
wlan type mgt and (subtype deauth or subtype disassoc)
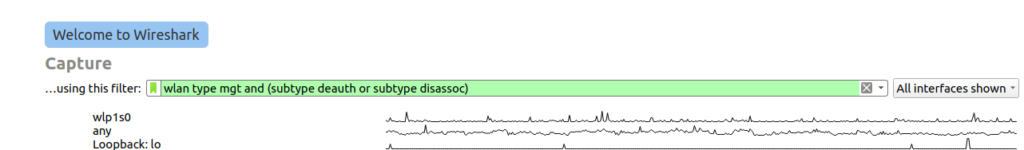
This sets the capture for management packets of sub-type de-auth or disassoc. These are used by popular tools to perform such attakcs.
Then add a view filter to isolate your router
wlan.bssid == AA:AA:AA:AA:AA
Prepare capture
Now you can start capturing packets. But let’s focus on the signal we are interested in. This will reduce the size of the capture data that might be saved on the disk in case you have a lot of network activity. Enter the following command (note that the 123 value below is my wifi network channel)
airodump-ng wlan0 -c 123
Now we can get back to wireshark.
Capturing packets
In wireshark, select the wireless lan interface then press the blue fin logo (or press ENTER) to start the capture. You will see the following screen
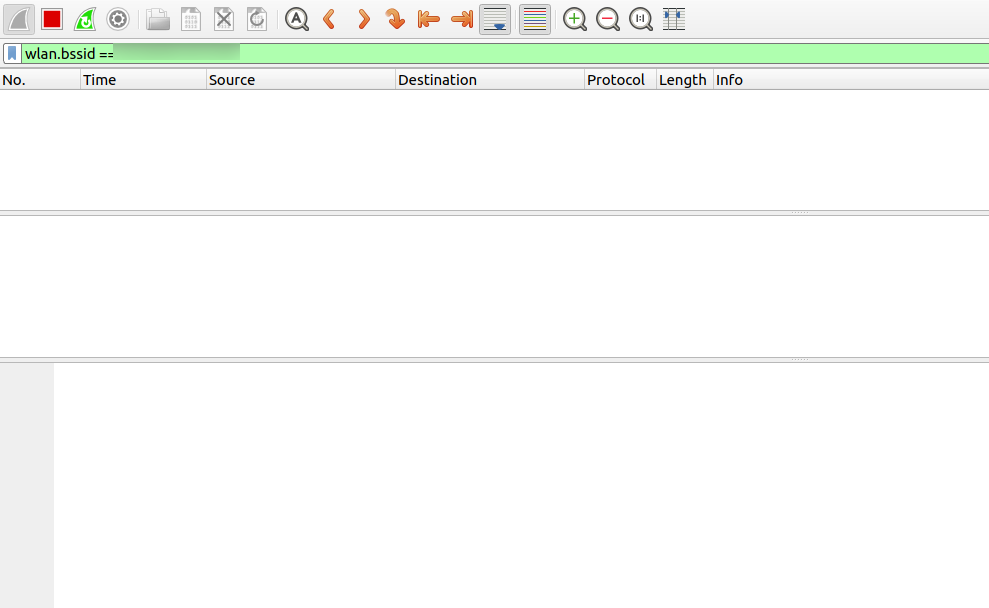
There are no data captured because no-one is running a de-auth attack. Let’s verify it is working well by sending some de-auth packets. Run the following command (note that wlan0 and AA:AA:AA:AA:AA:AA need to be changed accordingly to your network values)
aireplay-ng wlan0 --deauth 0 -a AA:AA:AA:AA:AA:AA
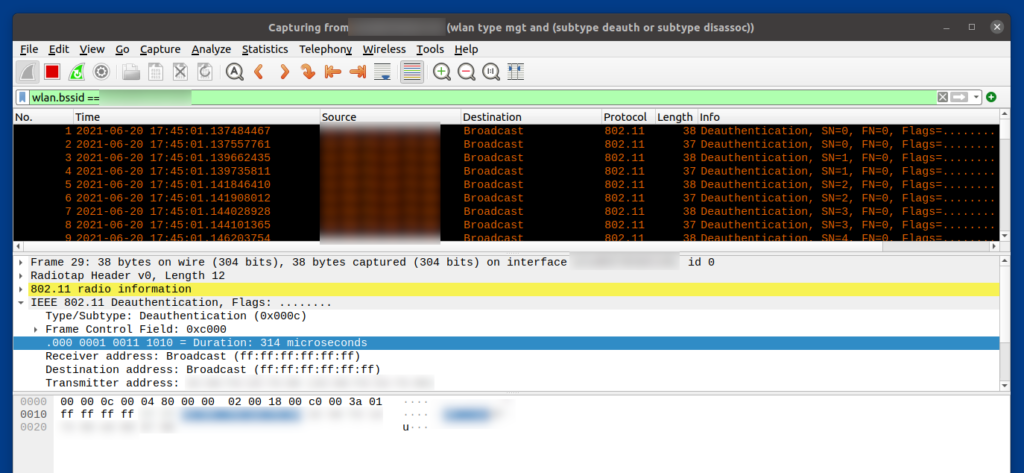
We can see the de-auth packet being sent over the network
Conclusion
Now you can also capture if someone is tempering with your network. I would like to create a Raspberry Pi scripted version of this capture and send alerts. I will post in this blog once I have something.
References
I used a lot of the following video from NULL-BYTE: https://www.youtube.com/watch?v=HYwsJJuAYqc
